Update: I've revised and split this post into two separate posts.
Cross-Site Request Forgery (CSRF) Attack: What It Is, How It Works, and How to Prevent It
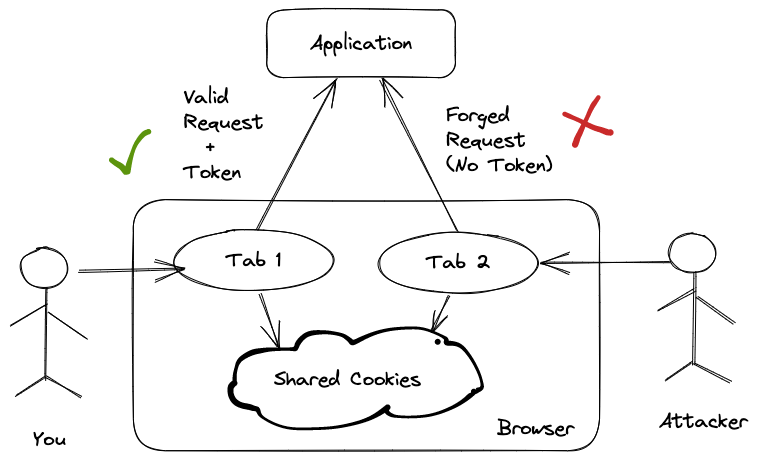
CSRF vulnerability tricks authenticated users of an application to perform a dangerous activity on that application, simply by clicking a link. This post explains how CSRF works with a practical example, and shows how to protect against it, both as a user and a developer building web applications.
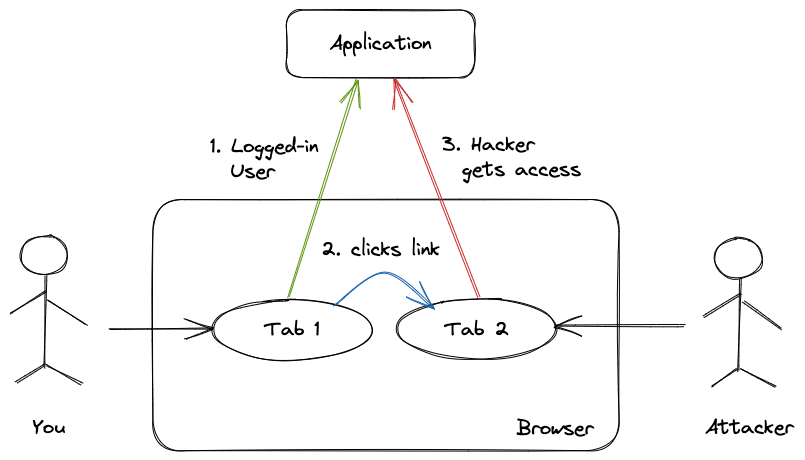
How Rails Authenticity Tokens Protect Against CSRF Vulnerability
Rails protects your web application from CSRF attack by including an authenticity token in the HTML forms. This token is also stored in the user’s session. Upon receiving a request, Rails compares these two tokens to decide if the request is verified.